The Federal Reserve Launches FedNow® Service
By Hannah Flanders
In 2022, research by the Pew Research Center found that over 75% of U.S. adults have utilized PayPal, Venmo, Zelle, or Cash App at least once to send and receive payments. Of these users, ease is cited as the main reason for their adoption.
As banks look to further engage their customers, remain competitive in a quickly advancing society, and provide a safe and trusted alternative to popular payment apps, the Federal Reserve has launched its long-awaited FedNow instant payment service.
What is FedNow?
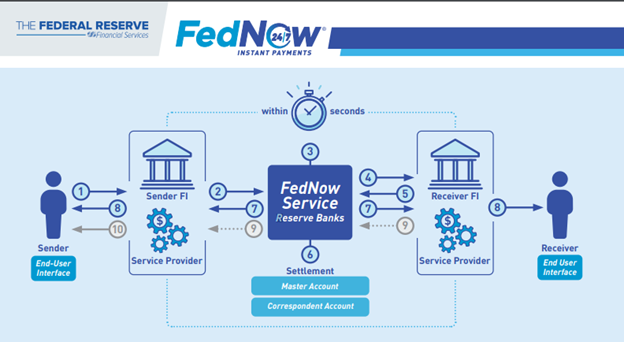
Launched in July 2023, FedNow allows financial institutions of all sizes to provide safe and efficient instant payment services to customers nationwide. Already, over 100 financial institutions across the U.S. have begun offering FedNow to customers. Of these institutions, First Citizens State Bank in Whitewater is currently one of the few in Wisconsin.
“As early adopters of the service, our team believes that FedNow, and other real-time payment systems, are the future of payments,” states Nate Parrish, First Citizens State Bank president. “We want to ensure our bank is on the cutting edge and not left behind when this technology really takes off.”
The release of the FedNow Service includes baseline functionality including core clearing and settlement capabilities. Currently, FedNow not only facilitates the peerto- peer (P2P) functionalities many customers are familiar with, but also has the capabilities to facilitate payments between businesses or between businesses and consumers. Further developments are expected to launch in phases as industry demand evolves.
FedNow, however, is not the first service to provide real-time payments to banks. In 2017, The Clearing House launched its Real Time Payments® (RTP) service to all federally insured U.S. depository institutions. As of mid-2023, over 350 banks and credit unions were listed as participants in RTP.
With several banks in Wisconsin signed on as RTP participants, the most significant difference bankers will notice with FedNow is the development of a new rail. The rail, which runs concurrent to already existing credit card and Automated Clearing House (ACH) payment rails, is overseen by the Federal Reserve Bank. Additionally, beginning in 2024, certified institutions will pay a monthly participation fee of $25. On the customer end, varying transaction limits (only $500,000 for Fed- Now) and clearing times occurring in just a matter of seconds may be the most obvious difference.
“‘Instant’ is the next modernization of ‘faster’ in the payments landscape,” says Julie Redfern, chief banking officer at Lake Ridge Bank in Monona. “Services such as Fedwire and FedACH, which are only available during certain windows, will always have a place. Fed- Now is the next step in remaining competitive and providing our customers the services they expect.”
For banks in deposit-gathering mode, the implementation of Fed- Now will help increase cash flow by allowing customers to move funds directly from one bank account to another, rather than storing funds within third-party apps. These capabilities to move money instantly can be found on the certified bank’s website or mobile app.
Getting Started
Unlike previous real-time systems, FedNow is generally seen as more accessible to mid-size and smaller banks. In this, smaller banks utilizing FedNow will now have the ability to access real-time payments without having to pay their larger competitors for the service.
Both First Citizens State Bank and Lake Ridge Bank, which is currently in the implementation process, are connecting to FedNow’s receiving rail (i.e., the bank cannot initiate customer payments) via integration of their core system. However, participation in the FedNow service is flexible, meaning that banks may opt to both send and receive payments, support liquidity management transfers, or access settlement services between correspondents and respondents. Additionally, banks may also choose to connect to the rail network through partnership with a FinTech company.
“FedNow has been slow out of the gate mainly due to bottlenecking on the core’s end,” says Redfern. “If an institution is considering going through a Fin- Tech, it’s important to make sure that they are already Fed approved rather than having to face additional delays.”
Parrish also emphasized the importance of getting ahead of the instant payment movement. “Especially with core providers being slow to adopt the idea of instantaneous movement, it may take several years for interested institutions to get on the rail. Even if 900 institutions are able to join in the next year, it could still take another nine or 10 years before FedNow is fully implemented across the country.”
To begin the process of implementation, banks are encouraged to consider their overarching payments plan and examine their operating processes to determine if the institution has the capabilities to support real-time payments. This process may require meeting with third party service providers or enhancing in-house technology.
From there, banks must undergo onboarding and testing. Certification, according to the Fed, is the final stage which entails the completion of an operational readiness test and network experience checklist. The Independent Community Bankers of America (ICBA) has emphasized that this process is not meant to be difficult, but rather to ensure that institutions are prepared to support instant payments.
The Future of FedNow
With just over 100 providers across the U.S. connected to FedNow’s rail as of October 2023, the main issue currently certified institutions are facing is the lack of transactions.
“Aside from conducting P2P payments, many customers are not entirely aware of the possibilities of FedNow,” says Parrish. “As bankers, it is our role to help inform our customers and small business clients of the possibilities of instant payments. From payroll to recurring bill payments or emergency disbursements, the ability to immediately move money will impact the way many operate.”
Though the Fed expects usage to increase as more institutions go live, banks that have incorporated FedNow into their payment offerings play an important role in emphasizing the key use cases and sharing with customers the possibilities of real-time payments.
Parrish also adds that the prospect of conducting Government-to- Consumer (G2C), Customer-to-Government (C2G), and Business-to-Government (B2G) payments on FedNow to be a significant factor as to why banks should become participants. Already, the U.S. Department of the Treasury’s Bureau of the Fiscal Service is ready with instant payment capabilities via FedNow.
Of course, as fraud continues to evolve, especially as increasingly more services become digitalized, risk mitigation and security is a significant consideration for many banks. While many theorize that the use of FedNow’s instant payment service will significantly cut down the number of uninsured, fraudulent payments that occur on third party apps as well as reduce check fraud scams across the country, it is vital that participating institutions have up-to-date strategies and procedures to mitigate risk.
Through FedNow, key risk management and information security solutions, such as accepting payments without posting, the ability to request more information from the sending or receiving institution, data encryption and tokenization, as well as several authentication and authorization measures, are available to participants. These tools, too, are expected to evolve and expand as the service grows. However, as the first line of defense against fraud, the Fed emphasizes that all participating institutions ensure that their overall fraud management strategy is consistent with the evolving payments landscape, communicated with vendors and customers, and regularly reviewed.
As ‘instant’ becomes the status quo for payments, FedNow can help drive commerce in new sectors, increase cash flow throughout communities, and offer financial institutions of all sizes innovative solutions to meeting the ever-evolving expectations of customers. To learn more about FedNow, and what its services may offer your bank and its customers, please visit frbservices.org/financial-services/fednow.
 By Daryll Lund
By Daryll Lund




 By Chris Schneider
By Chris Schneider

 By Rose Oswald Poels
By Rose Oswald Poels